-
Call Us:1.800.561.4019
Newsletter
For a Free Quote...
Latest Blog Posts
Blog Categories
Telnet Networks News
Retrospective Network Analysis
While network complexity and bandwidth demands continue to increase, new applications continue to be added increasing performance requirements. Now more than ever, network administrators require versatile monitoring and analysis tools to quickly troubleshoot business-critical operations and monitor security and compliance. In this environment, Retrospective Network Analysis (RNA) tools that let you go "back in time" to reconstruct a failure or attack can offer distinct advantages over analysis tools that only operate in real-time.
Background
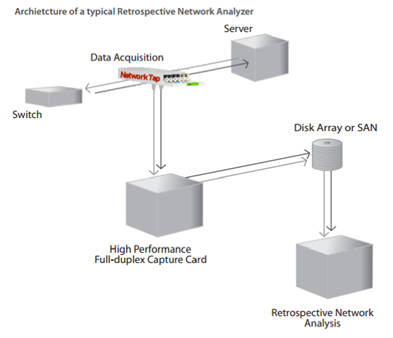
Retrospective network analysis (RNA) allows IT professionals to quickly browse backwards through massive amounts of network traffic. RNA allows network engineers to view breaches and anomalies exactly as they happened, within the context of other activity as it occurred on the network, thus sidestepping the often labor intensive step of trying to re-create problems to troubleshoot them. This requires that all network traffic (or some targeted subset) is efficiently captured and stored, in much the same way a convenience store might use a video security system.
So how does retrospective analysis function and why it offers a significant time and cost savings over conventional real-time analysis.
State of the Industry
The Concerns
With increased complexity and the volume of network traffic, the lack of information about network problems and being able to replicate a user problem as a recurring network issue becomes difficult.
How does RNA Work
RNA allows administrators a way to conduct analysis.
Traditional real-time packet capture and analysis gives network administrators insight into their networks via packet-level protocol decode and analysis. While these tools are certainly useful when managing any mid- to enterprise-level network, using them to provide administrators with enough information to solve subtle or sporadic problems is an arduous task. What's more, the ability to witness a compliance violation or security breach is limited to those lucky enough to be watching when it happens. RNA acts like a 24/7 surveillance camera —it is far easier to find the culprit using a stored video of the crime rather than just a photograph.
Example:
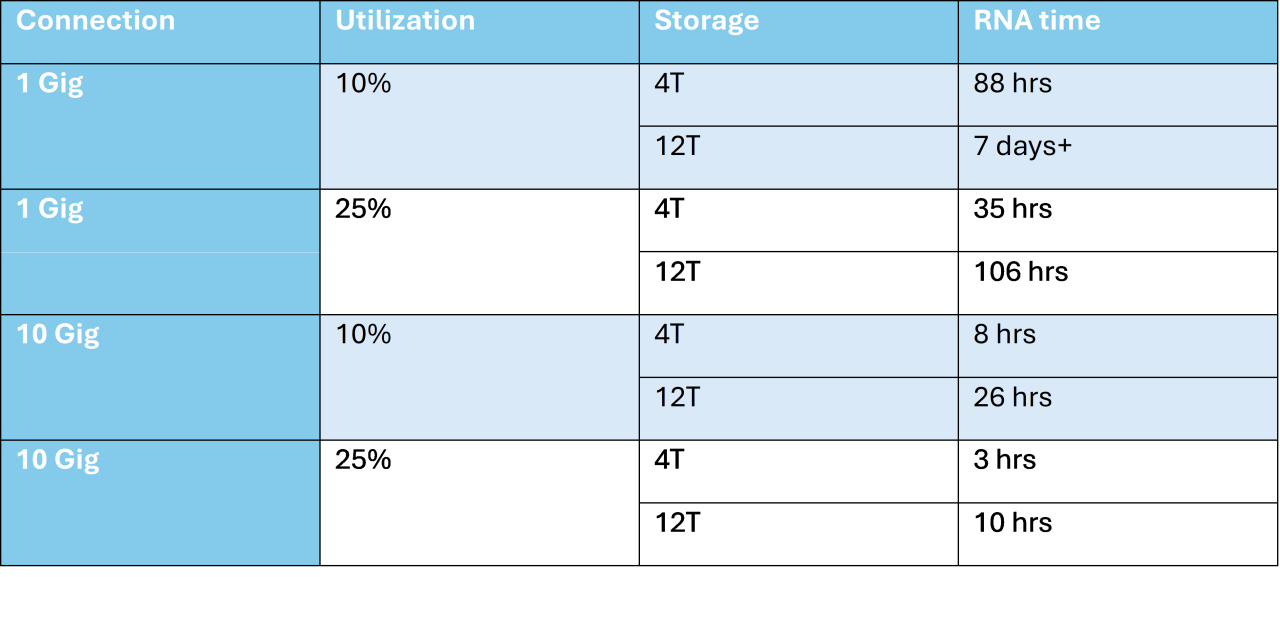
An RNA device is capable of storing terabytes of packet-level traffic collected from a variety of full-duplex network topologies, including WAN, LAN, Fibre Channel, wireless, gigabit, and 10 Gigabit (10 GbE). The appliance performs real-time Expert processing at the probe rather than transferring packet captures over the network to the console.
But there is more to RNA than just capturing and storing the traffic. To truly be useful, the tool should make it easy to find the relevant connection or time period as quickly as possible, further improving troubleshooting efficiency. RNA for the enterprise should also provide IT staff with the drill-down detail necessary for isolating problems to particular protocols, applications, servers, and stations. They should be flexible enough to monitor any topology, including LAN, WAN, WLAN, gigabit, 10 GbE, and Fibre Channel. For true network forensic analysis, the ability to reconstruct files, web pages, images, e-mails, and IMs; and compare breaches to Snort rules, is indispensable.
RNA can also be used for planning, rollout, and performance management stages for new applications, by taking advantage of monitoring and trending data to determine exactly how applications affect (or will affect) the network. Preliminary testing can save an enterprise the cost and headaches associated with a problematic application rollout.
Finally, the comprehensive functionality of RNA lets IT staff spend less time attempting to recreate problems and spend more time on proactive planning. In short, reduced downtime plus faster problem resolution equals a rapid return on investment.
Summary
Whereas traditional protocol analyzers have evolved over time, adding features and capabilities in a natural progression, RNA technology allows you to provide better service and improved security in a way that saves both time and money.
When considering the purchase of an RNA solution, look for products that provide the following features.
- Real-time analysis on the probe
- VoIP analysis and call scoring
- Stream or application reconstruction
- Multi-user, multi-session access
- Connection Dynamics
- Nanosecond resolution
- Seamless integration
- Option to offload to SAN
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.





Comments