-
Call Us:1.800.561.4019
Newsletter
For a Free Quote...
Latest Blog Posts
Blog Categories
Telnet Networks News
How to Optimize Your Security Defenses
As I mentioned in a blog a couple of months ago, there is an absolute myriad of security architectures and techniques available to the enterprise IT professionals. These strategies all have pros and cons. Lets look at one of the most common ones-a defensive approach.
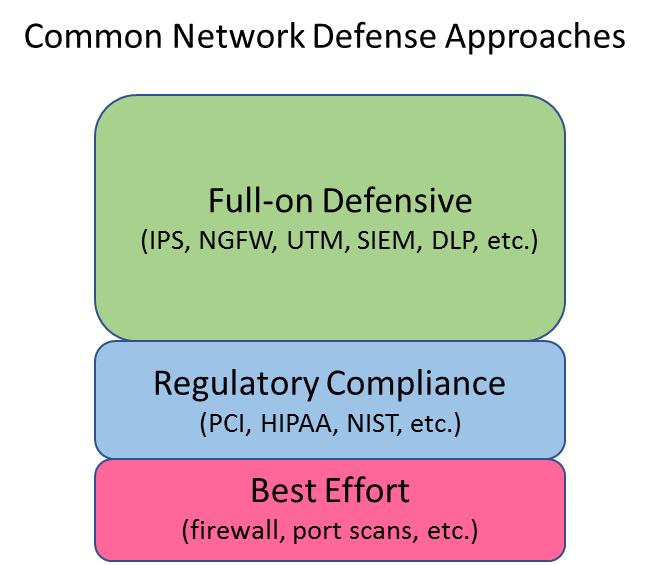
Everyone in the security arena is familiar with this concept. It is sometimes thought of as a three-tier level of security protection like the one shown here.
The first level most businesses consider is a "best effort" approach that uses one or two point solutions, like a firewall and maybe something else. A second strategy focuses on implementing what you need to achieve regulatory compliance (HIPAA, PCI, etc.). Some engineers and management teams used to think that this second level of security would make their networks secure. Unfortunately,they found out that your network can be PCI and HIPAA compliant and still get breached.
A full-on defensive approach is a third category of this network security approach and takes the concept to the next level. The focus here is on deploying as much technology as you can to defend your network from hackers. Examples include intrusion prevention systems (IPS), unified threat management (UTM), next generation firewalls (NGFW), web application firewalls (WAF), TLS/SSL decryption, honey pots, etc.
The full-on defensive approach is all about reducing your attack surface and deploying as many intrusion prevention solutions as possible. The whole goal is to stop as many attacks as possible and prevent a hacker from getting into the network.
Whether you agree or disagree with the philosophy that all attacks can be stopped is irrelevant. The reality is that everyone must deploy some sort of defense like this. If you don't, the business will be exposed to too much financial risk. For instance, should a breach occur and it is discovered that there was no attempt to stop attackers other than the deployment of a basic firewall, you may find yourself on unstable legal and financial ground during a lawsuit. The same is true for any government investigation into the breach. Decisions in both cases are based upon opinions—that is other people's opinions and not your own of what is a set of reasonable security defenses.
The short of it is—you need to do what is reasonably possible to prevent a breach of the network and prevent exfiltration of personally identifiable information (PII). This will help (key word is help, as it is not guaranteed) indemnify you during a breach investigation by legal authorities.
While this may sound like a lot of gloom and doom, a clear effort to implement a coherent defensive strategy will go a long way to strengthening your security architecture and reducing corporate risk.
For instance, here is a basic six-step approach to help you with securing your enterprise. More details are available in this whitepaper.
- Validate equipment readiness against malware and distributed denial of service (DDOS) attacks with a security threat tester
- Block traffic from known bad IP addresses
- Use inline real-time traffic analysis to search for hidden malware and security threats
- Decrypt data packets for better security inspection
- Perform advanced data filtering to improve analytics
- Enable deep packet inspection for threat detection and analysis
First, you need to test your equipment under real-world conditions and in real-world situations. Can your security equipment (firewalls, routers, etc.) handle denial of service (DOS), DDOS and malware attacks? What is the actual throughput your inline security tools (IPS, WAF, UTM, etc.) can handle under loaded network conditions? You need this information so that you can properly dimension equipment across your network. One note, this is different from penetration. This type of testing pushes your security equipment to its limit so that you get a very wide view of how they will respond against a variety of attacks.
Second, you should consider deploying a threat intelligence gateway to assist the firewall in blocking traffic from known bad IP addresses. This immediately reduces your chances of a successful attack. It also reduces the volume of data that your data inspection tools need to review. Reductions of up to 30% or more load on your inline tools are possible. One big difference with using an intelligence gateway is that you want the blocking access list to be constantly and automatically updated. While you could go in and manually update your firewall access list, this is far too time consuming and waste of your valuable time.
Real-time traffic analysis is an obvious component of a defensive strategy. Therefore, step three involves the use of inline security appliances. This is the IPS, WAF, etc. that I mentioned earlier, so I won't repeat those comments.
Nowadays, inspection of encrypted traffic is an almost "must have." This is the fourth step. It is commonly estimated that more than 50% of malware is disguised within encrypted traffic. If you don't inspect encrypted traffic, you just missed half of the threats that entered your network.
Step five involves using advanced data filtering techniques like application layer filtering. This let's include or exclude uninteresting data before it is sent to your security tools, like an intrusion detection system (IDS) or data loss prevention (DLP). For instance, if you don't want to inspect Hulu, Pandora, or Netflix traffic, simple filter that data out before the traffic is sent to your IDS. This allows you to literally cut the traffic volume that is sent to IDS by up to 35% or more. The other way of looking at this is that you are making your IDS 35% more efficient and allowing the IDS to inspect higher threat traffic quicker.
The last step is to use a network packet broker to focus on data capture for threat detection systems. While inline security tools can capture many types of threats, some will probably get by. Threat hunting allows you actively search for those threats and stop them before they can launch an attack.
You now have all the basic information that you need to start planning a defensive security architecture. If you want more information on this topic, read this whitepaper.
One note, there are always two sides to a coin. Defensive security (prevention) is one side. The other side is security resilience. This is the ability to deal with a breach correctly once it has happened. You can read more on security resilience here.
Thank you to Keith Bromely, of Ixia, a Keysight Business, for the article.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.




Comments