-
Call Us:1.800.561.4019
Newsletter
For a Free Quote...
Latest Blog Posts
Blog Categories
Telnet Networks News
Exposing the Ghost in the Virtual Machine
Virtualization continues to be an important data center success story. This technology has reduced physical plant hardware footprints, power costs, and cooling costs – significantly improving the total cost of ownership for the data center. At the same time, however, virtualization technology has also introduced a set of problems.
These problems have decreased the visibility into what is happening within the virtual network, and can be summarized as follows:
- Lack of visibility hides potential security and performance problems for a significant period of time
- Added additional network and monitoring complexity
- A lack of consistent monitoring policies between the physical and virtual networks
In case you think it’s just me saying this, Forrester Research performed a study for Cisco Systems on this subject and validated these three technology concerns, along with two additional concerns relating to manpower resourcing for virtualization technology. The chart below (from the Forrester virtualization security study) was a questionnaire that determined the actual virtualization issues and concerns for almost 80 IT decision makers.
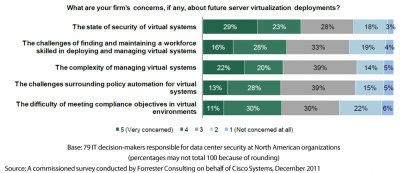
The first concern for data center managers was security. This is for good reasons. There are malware threats like “Crisis” that are capable of targeting virtual environments. Without proper visibility, these threats can gain a foothold and then flourish within your data center and you won’t even know it – until it’s too late. Another item related to this, but not mentioned in the Forrester study, is that performance problems can also be hidden by this lack of visibility. Without proper monitoring of virtual equipment, your data center may experience performance problems without you even knowing about them. Common examples include: slow traffic and devices, unnecessary bandwidth consumption, intermittent issues that pop-up long enough to be noticed but then disappear quickly, etc. Once the problems become noticeable, it’s often too late as something bad is normally going to happen. Hopefully it’s not an outage.
While virtualization introduced the benefit of the flexibility to spin up new virtual machines (VMs) almost at will, it has also caused complexity. Since the VMs can be spun up and down so quickly, it can become difficult to know what VMs exist, if and where they might have been moved to (in the case of VMware vMotion) and what policies, especially security policies, were set up for the VM’s when they were created. This rapid pace can end up creating “holes” that can be exploited by malware.
In addition, because most of the traffic (up to 80% according to Gartner) in the virtual data center never reaches the top of the rack, there are few, if any, network monitoring policies in place for the virtual equipment. This creates a huge blind spot where security and performance issues can hide. In short, you can’t monitor what you can’t measure.
Lastly, without access to the proper data, it can become exceedingly difficult to audit data and security policies for various compliance regulations (FISMA, HIPAA, PCI, etc.). So, you may be compliant on the physical side of the network but non-compliant on the virtual side. In the end, this makes you non-compliant which can have financial penalties as well as legitimate security risks.
In addition, a lack of a consistent monitoring policy often results from the natural division that has occurred between the physical and virtual infrastructure. IT physical infrastructures have been around for long enough that implementation and network monitoring policies have been tried and tested. So much so that best practices are commonly available. This is not the case for virtualized data centers. Monitoring policies are often non-existent and when they do exist, they are usually not aligned with the policies of the physical infrastructure. This is partially due to the lack of technology to properly expose the virtual data but it also comes about because the virtual data center is often run by a different department than the person(s) monitoring the physical data center. This means that the monitoring tool engineers often have little or no access to the virtual data center and can’t fold those systems into the overall network monitoring strategy.
These are the ghosts that hide within the virtual machine. While knowing that the ghosts exist is a start to exposing them, the real elimination of the problem is accomplished by installing a virtual Tap. Like it’s physical counterpart, the hardware-based Tap, a virtual Tap is software that is installed into the virtual data center so that data can be exported northbound and out of the data center to network packet brokers and monitoring tools that can then process and analyze the data.
Virtual Taps (like the Ixia Phantom vTap) can be used to remediate the issues mentioned earlier:
- Potential hidden security issues
- Provide access to data for trending
- Allow proper compliance policy tracking
At the same time, if the virtual Tap is integrated into a holistic visibility approach using a Visibility Architecture, you can streamline your monitoring costs because instead of having two separate monitoring architectures with potentially duplicate equipment (and duplicate costs), you have one architecture that maximizes the efficiency of all your current tools, as well any future investments. When installing the virtual Tap, the key is to make sure that it installs into the Hypervisor without adversely affecting the Hypervisor. Once this is accomplished, the virtual Tap will have the proper access to inter and intra-VMs that it needs, as well as the ability to efficiently export that information. After this, the virtual Tap will need a filtering mechanism so that exported data can be “properly” limited so as not to overload the LAN/WAN infrastructure. The last thing you want to do is to cause any performance problems to your network. Details on these concepts and best practices are available in the whitepapers Illuminating Data Center Blind Spots and Creating A Visibility Architecture.
As a side note, some people propose using the VMware vSphere “promiscuous mode” to get access to the data. This approach is fraught with danger as you expose the data to various security risks. In addition, using promiscuous mode might cause delays in transmitting data due to the overhead and summarizing processes. Normally, the best course of action is to use a dedicated Tap that can provide some level of QoS.
In my experience, bad things happen in blind spots and YOU don’t want to be the one to have to explain them to senior management. More information about the Ixia Phantom vTap and how it can help generate the insight needed for your business is available on the Ixia website.
Additional Resources:
White Paper: Illuminating Data Center Blind Spots
White Paper: Creating A Visibility Architecture
Thanks to Ixia for the article.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.





Comments