-
Call Us:1.800.561.4019
Newsletter
For a Free Quote...
Latest Blog Posts
Blog Categories
Telnet Networks News
Do You Really Know What’s Lurking in Your Data Center?
As mentioned in one of my previous blogs (Exposing The Ghost In The Virtual Machine), virtualization has been a great success story. At the same time, it holds hidden dangers that need to be managed. I want to take a couple minutes to outline those dangers and how to overcome them.
So, here are the dangers that can be hidden in a virtualized data center:
- Potential security issues due unknown malware
- Potential outages due to lack of proper performance data
- Regulatory compliance issues due to lack of adequate policy tracking
According to a study commissioned by Cisco Systems, 29% of the North American organizations surveyed identified the overall state of security of virtual systems as a major concern for future server virtualization deployments. This is for good reason. Cyber criminals are employing VM-aware malware that can spread unnoticed and unchecked among VMs due to lack of visibility between machines on the same server. This allows VM-aware malware to unknowingly spread to physical servers when moving VMs or applications. Without proper visibility, these threats can gain a foothold and then flourish within your data center – and you wouldn’t even know it.
Another concern is potential outages that can result from malware or other issues within the data center (problematic software upgrades, overloaded equipment and links, and programming mistakes). Common symptoms of performance problems can include: slow traffic and devices, unnecessary bandwidth consumption, and intermittent issues that pop-up long enough to be noticed but then disappear quickly. By the time you recognize the symptoms, it’s often too late as the problems have the ability to be service affecting. Proper performance monitoring mitigates this concern by allowing IT managers to perform trend analysis and monitor single points of failure – like load balancers, cloud services, WAN optimizers, etc.
Regulatory compliance is a third fundamental concern. Much emphasis has been placed on this topic over the last several years, and while you may have everything in order on the physical components of your network, it’s often harder to square away the virtualized portion of the network. One of the main reasons is audit validation. What’s your current plan to know if you are compliant with all applicable regulations (e.g., FISMA, HIPAA, PCI, etc.)? And do you have the proper access to data in the virtualized portion of your network to prove that you are compliant? The business concern, of course, is that if one portion of your network is non-compliant then the company is non-compliant (or partially compliant, if you have some marketing spin leeway!).
The key question is how do you find the source of the hidden dangers within your virtual network? Your primary target should be the data center. According to a study by Gartner, up to 80% of the traffic in a virtualized data center never makes it to the top of the rack, where conventional monitoring practices like packet brokers and monitoring tools can capture the data. So, are you sure you know what’s happening in your data center before this point? Most data center managers don’t.
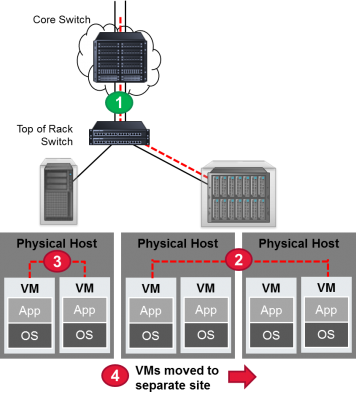 This diagram should make it a little clearer. It shows the four key visibility points in a virtual network. Point number 1 isn’t a problem. Since the data is transferred from the equipment in one rack to another, this gives the data center administrator an opportunity to use a physical tap to access the data. But for situations 2 through 4, there is no easy access with standard taps and monitoring tools.
This diagram should make it a little clearer. It shows the four key visibility points in a virtual network. Point number 1 isn’t a problem. Since the data is transferred from the equipment in one rack to another, this gives the data center administrator an opportunity to use a physical tap to access the data. But for situations 2 through 4, there is no easy access with standard taps and monitoring tools.
In the case of point number 2, there is limited visibility within the server chassis. The traffic across the backplane isn’t accessible by traditional monitoring tools.
In case number 3, the traffic passes between VMs within the same physical host. In this case, everything is handled strictly through software. So again, there is no opportunity for traditional monitoring tools and practices to help.
And in case number 4 (when VMs are moved) any access to the VM that might have been established is typically lost.
Points 2 through 4 are what we mean when we talk about the opportunity for blind spots to exist. The blind spots are where the hidden dangers lurk. Traditional monitoring tools won’t help as they don’t give you access to the data in this portion of the network.
So now we see the problem, but how do you fix it? A virtual tap is often one of the best solutions. They are cost effective pieces of software that can be installed directly into the virtual data center. They function in a similar manner as a physical tap in that they replicate traffic and forward that data on. This gives you the access points you need to forward traffic out of the data center and towards your standard monitoring gear, like packet brokers and specialized monitoring analysis tools.
One note, not all virtual taps are created equal. You probably want to make sure that the virtual tap performs some level of filtering so that the replicated traffic isn’t a complete copy of everything in your data center. Otherwise, you’ll overload the LAN. Also, you’ll want hypervisor plug-in capability to maximize your access to the virtual traffic. Lastly, consider virtual taps that have minimal performance impacts on the hypervisor or you can actually create potential performance problems. There are products on the market that perform all three functions.
Once the virtual tap(s) is inserted into you data center, you’ll have the data you need to implement proactive, instead of reactive, approaches to problem resolution and security threats. You’ll also be able to implement the same internal security and monitoring policies across your network which should help greatly with work flows, problem resolution capabilities and even costs.
Ixia makes a virtual tap product called the Ixia Phantom vTap. More information about the Ixia Phantom vTap and how it can help generate the insight needed for your business is available on the Ixia website.
Additional Resources:
Illuminating Data Center Blind Spots
Increased Visibility and Monitoring of Virtual Systems
Creating A Visibility Architecture
Thanks to Ixia for the article.
When you subscribe to the blog, we will send you an e-mail when there are new updates on the site so you wouldn't miss them.




Comments